CCNA 5.0 (CCNA R&S) – Switched Networks Final Exam P1
1
What term is used to describe a hierarchical model in which three layers are not needed?
three-tier model
collapsed core
distribution-access model
dual-core model
2
Where in the Cisco Borderless Architecture is the forwarding rate crucial?
at access layer only
at all layers
at core layer only
at distribution and core layers only
at distribution layer only
3
Which factor can limit the implementation of a converged network infrastructure?
QoS implementation
software-based phones
legacy equipment
point-to-point video traffic
4
When would a network designer be concerned with RUs?
when considering port density
when calculating maximum port speed
when determining the number of available line cards
when purchasing a specific number of switches for a network rack
CCNA 5.0 (CCNA R&S) – Switched Networks Final Exam P1
5
What is the PoE pass-through feature?
how the power is supplied for a stack of switches
how the switch supplies electrical power to all of the line cards that are connected to it
the capability of a wireless AP to supply electrical power to IP phones
the capability of powering the switch as well as any devices that are directly connected to the switch
6
When a fixed configuration switch is purchased for use on a new network infrastructure, which feature would be of most value if the network is characterized as having a large numbers of users but the users require little bandwidth?
PoE pass-through
wire speed
PoE
port density
7
Which switching method results in the lowest latency when forwarding frames?
fast forward
fragment free
store and forward
symmetric
8
Which impact does adding a Layer 2 switch have on a network?
an increase in the number of dropped frames
an increase in the size of the broadcast domain
an increase in the number of network collisions
an increase in the size of the collision domain
9
Using default settings, what is the next step in the switch boot sequence after the IOS loads from flash?
Perform the POST routine.
Search for a backup IOS in ROM.
Load the bootstrap program from ROM.
Load the running-config file from RAM.
Locate and load the startup-config file from NVRAM.
CCNA 5.0 (CCNA R&S) – Switched Networks Final Exam P1
10
An administrator needs management access to a switch from a remote offsite location. Which three configurations are required on the switch to allow the administrator to have remote access using either SSH or Telnet? (Choose three.)
default gateway
banner message
VLAN IP address
vty line password
encrypted passwords
console line password
11
What impact does the use of the mdix auto configuration command have on an Ethernet interface on a switch?
automatically detects duplex settings
automatically detects interface speed
automatically detects copper cable type
automatically assigns the first detected MAC address to an interface
12
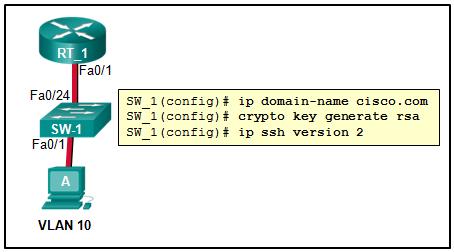
Refer to the exhibit. Which two commands or groups of commands are needed to complete the switch configuration so that SSH can be used to telnet from host A to SW_1? (Choose two.)
SW_1(config)# username david password class
SW_1(config)# line vty 0 15
SW_1(config-line)# login
SW_1(config-line)# password cisco
SW_1(config)# line vty 0 15
SW_1(config-line)# login local
SW_1(config-line)# transport input ssh
SW_1(config)# login ssh
SW_1(config)# password class
SW_1(config)# login key rsa
SW_1(config)# password cisco
SW_1(config)# password encrypted cisco
13
Which attack allows the attacker to see all frames on a broadcast network by causing a switch to flood all incoming traffic?
LAN storm
VLAN hopping
STP manipulation
MAC table overflow
802.1q double tagging
14
Which two statements are true about VLAN implementation? (Choose two.)
The size of the collision domain is reduced.
The number of required switches in a network decreases.
VLANs logically group hosts, regardless of physical location.
The network load increases significantly because of added trunking information.
Devices in one VLAN do not hear the broadcasts from devices in another VLAN.
15
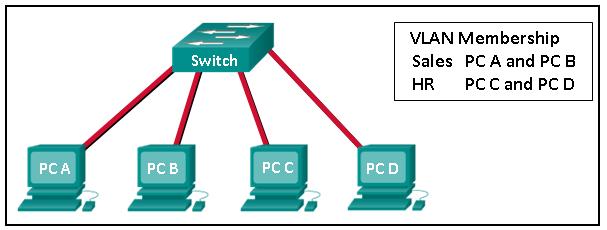
Refer to the exhibit. Two VLANs have been configured on the switch and PCs have been assigned. PCs in the Sales VLAN can ping all PCs in their own VLAN, but cannot ping the PCs in the HR VLAN. What are two explanations for this problem? (Choose two.)
All PCs are in one collision domain.
All PCs are in one broadcast domain.
A router is required for communication between VLANs.
The PCs are in separate broadcast domains.
The management VLAN has not been assigned an IP address.
16
Refer to the exhibit. What is the purpose of the configuration commands that are shown?
to activate port Fa0/10
to make the port a member of VLAN 30
to activate port security on port Fa0/10
to add VLAN 30 to the trunk that is connected to port Fa0/10
17
Which two commands should be implemented to return a Cisco 3560 trunk port to its default configuration? (Choose two.)
S1(config-if)# no switchport trunk allowed vlan
S1(config-if)# no switchport trunk native vlan
S1(config-if)# switchport mode dynamic desirable
S1(config-if)# switchport mode access
S1(config-if)# switchport access vlan 1
18
Which three pairs of trunking modes will establish a functional trunk link between two Cisco switches? (Choose three.)
dynamic desirable – dynamic desirable
dynamic auto – dynamic auto
dynamic desirable – dynamic auto
dynamic desirable – trunk
access – trunk
access – dynamic auto
19
Under which two occasions should an administrator disable DTP while managing a local area network? (Choose two.)
when connecting a Cisco switch to a non-Cisco switch
when a neighbor switch uses a DTP mode of dynamic auto
when a neighbor switch uses a DTP mode of dynamic desirable
on links that should not be trunking
on links that should dynamically attempt trunking
20
While analyzing log files, a network administrator notices reoccurring native VLAN mismatches. What is the effect of these reoccurring errors?
All traffic on the error-occurring trunk port is being misdirected or dropped.
The control and management traffic on the error-occurring trunk port is being misdirected or dropped.
All traffic on the error-occurring trunk port is being switched correctly regardless of the error.
Unexpected traffic on the error-occurring trunk port is being received.
21
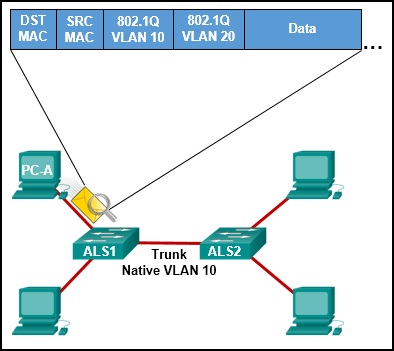
Refer to the exhibit. An attacker on PC-A sends a frame with two 802.1Q tags on it, one for VLAN 10 and another for VLAN 20. What will happen to this frame?
It will be dropped by ALS1 because it is invalid.
ALS1 will leave both tags on the frame and send it to ALS2, which will forward it to hosts on VLAN 10.
ALS1 will remove both tags and forward the rest of the frame across the trunk link, where ALS2 will forward the frame to hosts on VLAN 10.
ALS1 will remove the outer tag and send the rest of the frame across the trunk link, where ALS2 will forward the frame to hosts on VLAN 20.
22
Which two methods can be used to provide secure management access to a Cisco switch? (Choose two.)
Configure all switch ports to a new VLAN that is not VLAN 1.
Configure specific ports for management traffic on a specific VLAN.
Configure SSH for remote management.
Configure all unused ports to a “black hole.”
Configure the native VLAN to match the default VLAN.
23
What is the purpose of the Spanning Tree Protocol (STP)?
prevents Layer 2 loops
prevents routing loops on a router
creates smaller collision domains
creates smaller broadcast domains
allows Cisco devices to exchange routing table updates
24
A set of switches is being connected in a LAN topology. Which STP bridge priority value will make it least likely for the switch to be selected as the root?
4096
32768
61440
65535
25
What two STP features are incorporated into Rapid PVST+? (Choose two.)
UplinkFast
PortFast
BPDU guard
BPDU filter
BackboneFast
loop guard
26
Which statement is true regarding states of the IEEE 802.1D Spanning Tree Protocol?
Ports are manually configured to be in the forwarding state.
Ports listen and learn before going into the forwarding state.
Ports must be blocked before they can be placed in the disabled state.
It takes 15 seconds for a port to go from blocking to forwarding.
27
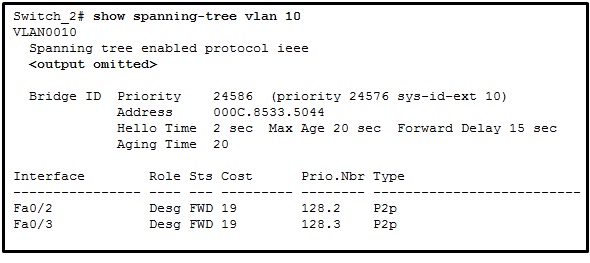
Refer to the exhibit. A network administrator is verifying the bridge ID and the status of this switch in the STP election. Which statement is correct based on the command output?
The bridge priority of Switch_2 has been lowered to a predefined value to become the root bridge.
The bridge priority of Switch_2 has been lowered to a predefined value to become the backup root bridge.
The STP instance on Switch_2 is failing due to no ports being blocked and all switches believing they are the root.
The STP instance on Switch_2 is using the default STP priority and the election is based on Switch_2 MAC address.
28
An STP instance has failed and frames are flooding the network. What action should be taken by the network administrator?
A response from the network administrator is not required because the TTL field will eventually stop the frames from flooding the network.
Spanning tree should be disabled for that STP instance until the problem is located.
Broadcast traffic should be investigated and eliminated from the network.
Redundant links should be physically removed until the STP instance is repaired.
29
When the show spanning-tree vlan 33 command is issued on a switch, three ports are shown in the forwarding state. In which two port roles could these interfaces function while in the forwarding state? (Choose two.)
disabled
designated
root
alternate
blocked
30
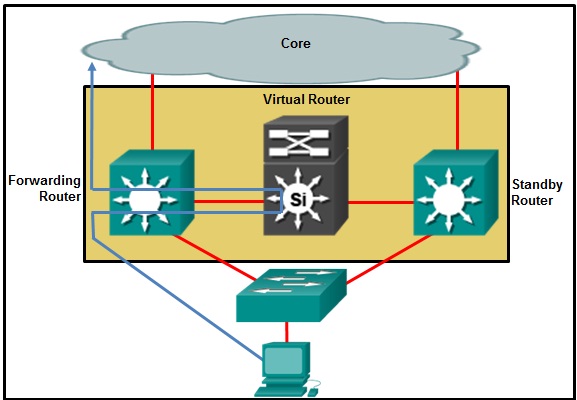
Refer to the exhibit. Which destination MAC address is used when frames are sent from the workstation to the default gateway?
MAC address of the forwarding router
MAC addresses of both the forwarding and standby routers
MAC address of the standby router
MAC address of the virtual router
P2