CCNA 5.0 (CCNA R&S) – Network Basics Final Exam P2
26
Which two statements correctly describe a router memory type and its contents? (Choose two.)
ROM is nonvolatile and stores the running IOS.
FLASH is nonvolatile and contains a limited portion of the IOS.
RAM is volatile and stores the IP routing table.
NVRAM is nonvolatile and stores other system files.
ROM is nonvolatile and contains basic diagnostic software.
27
In which default order will a router search for startup configuration information?
NVRAM, RAM, TFTP
NVRAM, TFTP, setup mode
setup mode, NVRAM, TFTP
TFTP, ROM, NVRAM
flash, ROM, setup mode
28
Which IP address is a valid host address?
172.16.4.32/27
172.16.4.79/28
172.16.4.255/22
172.16.5.255/23
29
Which three IP addresses are private ? (Choose three.)
10.1.1.1
172.32.5.2
192.167.10.10
172.16.4.4
192.168.5.5
224.6.6.6
30
What is the purpose of ICMP messages?
to inform routers about network topology changes
to ensure the delivery of an IP packet
to provide feedback of IP packet transmissions
to monitor the process of a domain name to IP address resolution
31
What is the range of host IP addresses for the subnet 172.16.1.32/29?
172.16.1.33 – 172.16.1.38
172.16.1.33 – 172.16.1.46
172.16.1.33 – 172.16.1.62
172.16.1.32 – 172.16.1.39
172.16.1.32 – 172.16.1.47
32
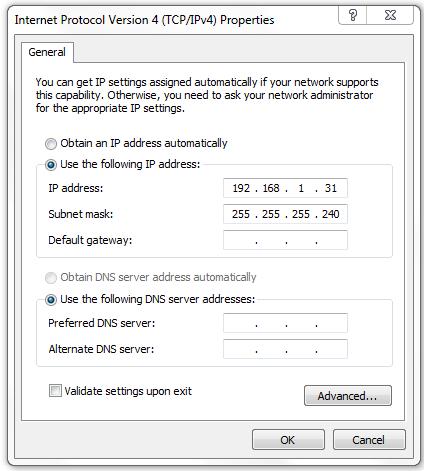
Refer to the exhibit. A user is configuring a PC with the IP settings as displayed, but the operating system will not accept them. What is the problem?
The subnet mask is wrong.
The IP address is not a usable host address.
The DNS settings are not configured.
The gateway address is not configured.
33
Which subnet would include the address 192.168.1.96 as a usable host address?
192.168.1.64/26
192.168.1.32/27
192.168.1.32/28
192.168.1.64/29
34
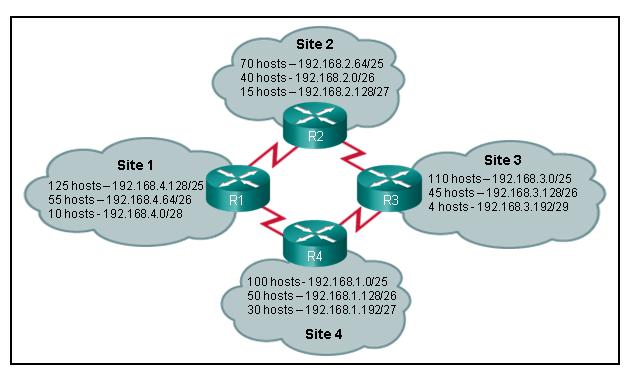
Refer to the exhibit. Which IP addressing scheme should be changed?
Site 1
Site 2
Site 3
Site 4
35
An organization has received the IPv6 network prefix of 2001:db8:1234::/48 from their ISP. How many subnets can be created from this prefix without borrowing bits from the interface ID?
1024
4096
8192
65536
36
What is a characteristic of the LLC sublayer?
It provides the logical addressing required that identifies the device.
It provides delimitation of data according to the physical signaling requirements of the medium.
It places information in the frame that allows multiple Layer 3 protocols to use the same network interface and media.
It defines software processes that provide services to the physical layer.
37
Which media access method requires that an end device send a notification across the media before sending data?
CSMA/CA
CSMA/CD
deterministic
token passing
38
A frame is transmitted from one networking device to another. Why does the receiving device check the FCS field in the frame?
to determine the physical address of the sending device
to verify the network layer protocol information
to compare the interface media type between the sending and receiving ends
to check the frame for possible transmission errors
to verify that the frame destination matches the MAC address of the receiving device
39
What is an important function of the physical layer of the OSI model?
It accepts frames from the physical media.
It encapsulates upper layer data into frames.
It defines the media access method performed by the hardware interface.
It encodes frames into electrical, optical, or radio wave signals.
40
Which procedure is used to reduce the effect of crosstalk in copper cables?
requiring proper grounding connections
twisting opposing circuit wire pairs together
wrapping the bundle of wires with metallic shielding
designing a cable infrastructure to avoid crosstalk interference
avoiding sharp bends during installation
41
What are the three primary functions provided by Layer 2 data encapsulation? (Choose three.)
error correction through a collision detection method
session control using port numbers
data link layer addressing
placement and removal of frames from the media
detection of errors through CRC calculations
delimiting groups of bits into frames
conversion of bits into data signals
42
A PC is configured to obtain an IP address automatically from network 192.168.1.0/24. The network administrator issues the arp –a command and notices an entry of 192.168.1.255 ff-ff-ff-ff-ff-ff. Which statement describes this entry?
This is a static map entry.
This is a dynamic map entry.
This entry refers to the PC itself.
This entry maps to the default gateway.
43
What will a Layer 2 switch do when the destination MAC address of a received frame is not in the MAC table?
It initiates an ARP request.
It broadcasts the frame out of all ports on the switch.
It notifies the sending host that the frame cannot be delivered.
It forwards the frame out of all ports except for the port at which the frame was received.
44
What is the auto-MDIX feature on a switch?
the automatic configuration of an interface for 10/100/1000 Mb/s operation
the automatic configuration of an interface for a straight-through or a crossover Ethernet cable connection
the automatic configuration of full-duplex operation over a single Ethernet copper or optical cable
the ability to turn a switch interface on or off accordingly if an active connection is detected
45
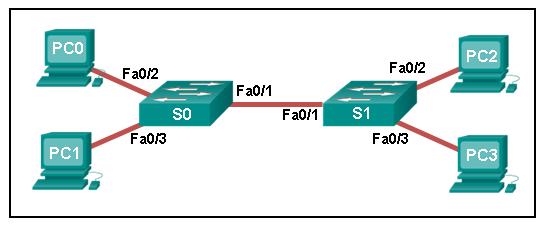
Refer to the exhibit. A ping to PC3 is issued from PC0, PC1, and PC2 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?
just PC0 and PC1 MAC addresses
just the PC0 MAC address
PC0, PC1, and PC2 MAC addresses
just the PC1 MAC address
just the PC2 MAC address
46
In performing a protocol analysis of a network, when should traffic be captured to ensure the most accurate representation of the different traffic types on the network?
during software upgrades
during times of moderate network use
during hours of peak network use
during weekends and holidays when network use is light
47
How does a Layer 3 switch differ from a Layer 2 switch?
A Layer 3 switch supports VLANs, but a Layer 2 switch does not.
An IP address can be assigned to a physical port of a Layer 3 switch. However, this is not supported in Layer 2 switches.
A Layer 3 switch maintains an IP address table instead of a MAC address table.
A Layer 3 switch learns the MAC addresses that are associated with each of its ports. However, a Layer 2 switch does not.
48
A network administrator is checking the system logs and notices unusual connectivity tests to multiple well-known ports on a server. What kind of potential network attack could this indicate?
access
reconnaissance
denial of service
information theft
49
What is the most effective way to mitigate worm and virus attacks?
Secure all Layer 2 devices.
Ensure that users change their passwords often.
Deploy packet filtering firewalls at the network edge.
Install security updates to patch vulnerable systems.
50
When applied to a router, which command would help mitigate brute-force password attacks against the router?
exec-timeout 30
service password-encryption
banner motd $Max failed logins = 5$
login block-for 60 attempts 5 within 60
51
A particular website does not appear to be responding on a Windows 7 computer. What command could the technician use to show any cached DNS entries for this web page?
ipconfig /all
arp -a
ipconfig /displaydns
nslookup
52
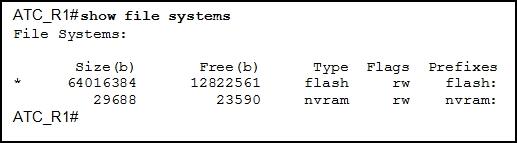
Refer to the exhibit. What is the significance of the asterisk (*) in the exhibited output?
The asterisk shows which file system was used to boot the system.
The asterisk designates which file system is the default file system.
An asterisk indicates that the file system is bootable.
An asterisk designates that the file system has at least one file that uses that file system.
53
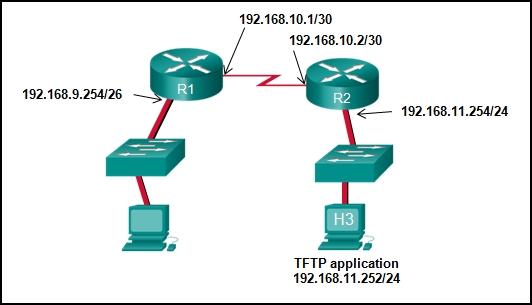
Refer to the exhibit. The network administrator enters these commands into the R1 router:
R1# copy running-config tftp
Address or name of remote host [ ]?
When the router prompts for an address or remote host name, what IP address should the administrator enter at the prompt?
192.168.9.254
192.168.10.1
192.168.10.2
192.168.11.252
192.168.11.254
54
Fill in the blank.
During data communications, a host may need to send a single message to a specific group of destination hosts simultaneously. This message is in the form of a …………………………. message.
55
Fill in the blank. Use the acronym.
A VoIP call uses ………………… as the Layer 4 protocol.
56
57
58
59
Open the PT activity. Perform the tasks in the activity instructions and then fill in the blank.
The Server0 message is …………….
60
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which IPv6 address is assigned to the Serial0/0/0 interface on RT2?
2001:db8:abc:1::1
2001:db8:abc:5::1
2001:db8:abc:5::2
2001:db8:abc:10::15